Oracle Integration Cloud (OIC) is Oracle’s next generation modern Integration solution Platform as a Service (PaaS) offering. The core purpose of this product to integrate various SaaS and On-prem systems real time. In addition to Integration capability, it also provides Process Automation and Visual Builder Capability. Details docs are available here.
OIC has concept of Adapters. There are huge range of adapters available and documented here.
One of the Adapter REST Adapter been used to expose an Integration to outside world for consumption. In order word, it’s an entry point for most of Integrations what we developed using OIC. It also gets used to invoke any external REST based endpoint.
REST Adapter support Basic Auth and various flavour of OAuth as security mechanism to protect the Integration access.
However, not all OAuth flavour supported for Trigger Role (Used as Entry point of Integration) vs Invoke Role (Used for invoking third party REST endpoint).
REST APIs exposed using the REST Adapter (Trigger Role) are protected using Basic Authentication and OAuth token-based authentication.
REST API consumed using the REST Adapter (Invoke Role) Support HTTP Basic Authentication, OAuth Client Credentials (two-legged flow), OAuth Resource Owner Password Credentials (two-legged flow), OAuth Authorization Code Credentials (three-legged flow), OAuth Custom Three Legged Flow, OAuth Custom Two Legged Flow, OAuth 1.0a One Legged Authentication, Amazon Web Services (AWS) Signature Version 4, and Oracle Cloud Infrastructure (OCI) Signature Version 1. There is also support for consuming APIs that are unprotected.
Now, majority of Customers chose Basic AUTH while publishing an Integration because it’s very simply to implement but has limitation because the user password gets expired in every 3 month which result changing all Integrations configuration again in 3 month of time. We can very well avoid this problem by Implementing OAuth token which never gets expired.
Oracle has official document for setting up Service Account without expiry but it’s quite difficult to follow instructions from that document. Hence, I thought to publish more user friendly instructions to achieve the same outcome.
In this blog, I will be covering how we can invoke an Integration exposed using REST Adapter (Trigger role) using OAuth token which doesn’t get expired.
To implement this solution we also need to understand Oracle Identity Cloud Service concept which is IAM solution for all Oracle PaaS services.
Before I proceed anything further, I would like to thanks Callan HP who helped me during this POC.
In order to setup the whole flow below activities will be performed.
- Getting an access token which is used to invoke the IDCS REST API
- Create an OAuth application in IDCS for Integration Service Account Purpose
- Associate newly created IDCS Application to OIC
- Test Hello Word OIC Integration using OAuth Client ID and Client Secret
Getting an access token which is used to invoke the IDCS REST API
Note: You should have at least Application Administrator access to your Identity Cloud Service to achieve below task.
Login to cloud.oracle.com using your credentials and Customer account and navigate to Identity >> Federation >> click Oracle Identity Cloud Service URL to open the IDCS Admin Console.
At rightmost top corner, click on user account and then click further on “My Access Token”
Another window will open, and after selecting which roles you want a token for (the next step requires at least “Application Administrator”), you with be able to obtain a token by clicking the “Download Token” button at the rightmost corner.

It will download a file tokens.tok which will contain an access token in a JSON wrapper. Copy the value of the “app_access_token” attribute, as shown below.
Now, we got the IDCS token which can be used to invoke the IDCS REST API to create a new IDCS Application. To know more about IDCS Confidential application refer to the documentation.
Create an OAuth application in IDCS for Integration Service Account Purpose
Next step is to create IDCS Confidential Application by using IDCS REST API.
REST API Syntax (using curl):
curl -X POST https://${IDCS_HOST}/admin/v1/Apps -H 'Authorization: Bearer ${ACCESS_TOKEN}'
-H 'Content-Type: application/json' -d '{$PAYLOAD}'Sample Variable Values are:-
${IDCS_HOST} – This value is hostname of IDCS which can be copied of IDCS URL as per above steps. Sample value look like this – https://idcs-231exxxxxxxxxx.identity.oraclecloud.com/
${ACCESS_TOKEN} = This is value of the app_access_token attribute which we got from tokens.tok file.
${PAYLOAD} = Change “displayName” and “name” element values as per your choice. The “name” attribute must end with “_BASICAUTH” to be used with OIC.
"active": true,
"isOAuthClient": true,
"allowedGrants": ["client_credentials"],
"basedOnTemplate": {
"value": "CustomWebAppTemplateId" },
"clientType": "confidential",
"displayName": "<Your App name here>",
"name": "<app_name>_BASICAUTH",
"schemas": ["urn:ietf:params:scim:schemas:oracle:idcs:App"]
So, final API will look something like this –
curl -X POST https://idcs-231e1exxxxxxxxxx.identity.oraclecloud.com/admin/v1/Apps -H 'Authorization: Bearer eyJ4NX...' -H 'Content-Type: application/json' -d '{ "active": true, "isOAuthClient": true,"allowedGrants": ["client_credentials"],"basedOnTemplate": {"value": "CustomWebAppTemplateId"}, "clientType": "confidential", "displayName": "mgu_OIC_SVC_ACC_BASICAUTH", "name": "mgu_OIC_SVC_ACC_BASICAUTH", "schemas": ["urn:ietf:params:scim:schemas:oracle:idcs:App"]}'
Once executed successfully from any terminal, it will give response stating application created successfully.

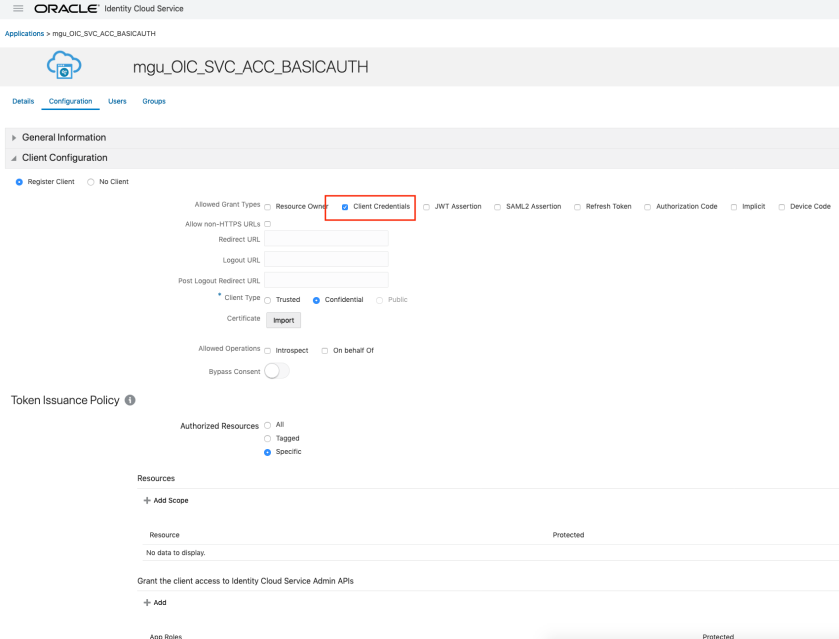
Login to IDCS console, go to application menu and verify newly created application. In my case it was “mgu_OIC_SVC_ACC_BASICAUTH”
Make a note of client Id and client secret. We will be using this to invoke OIC Integration.
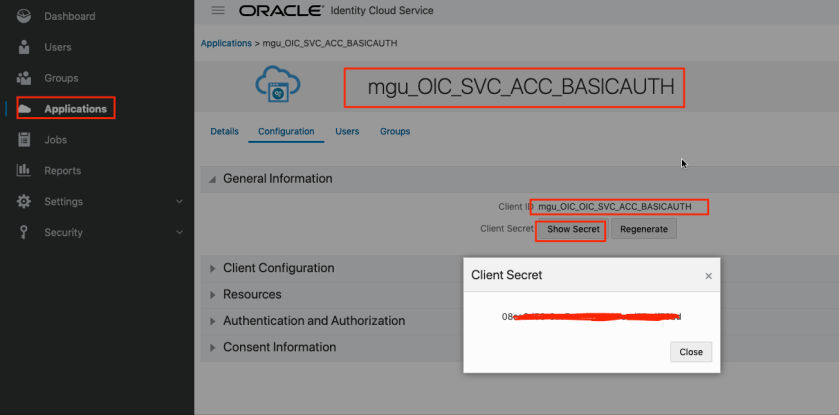
Also note the we have allowed “Client Credential” type of grant to this application.
Associate newly created IDCS Application with OIC
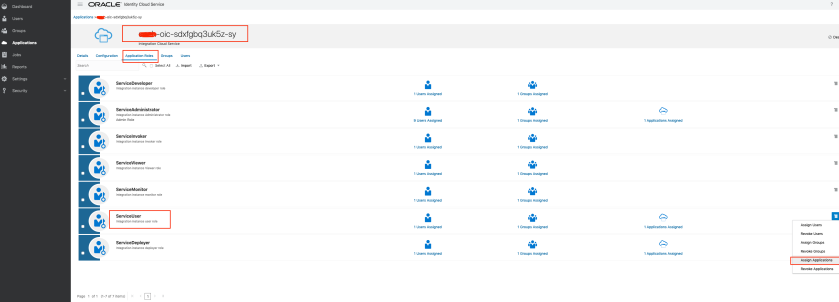
The next step is to associate this confidential application with an OIC application ServiceUser role. This role gets created by default during OIC provisioning, and can be managed in IDCS.
In order to assign the new application this role, find your OIC Application in IDCS. If your OIC Instance name is something like xxx-oic, the corresponding IDCS application name is xxx-oic-abcdef12345-sy. The quickest way to locate this is probably to type your instance name in the search bar at the top right of the Applications list.
Once you have found the corresponding application, open it, and go to “Application Roles”. The select the hamburger menu on the right of the “ServiceUser” role, and select “Assign Application”.
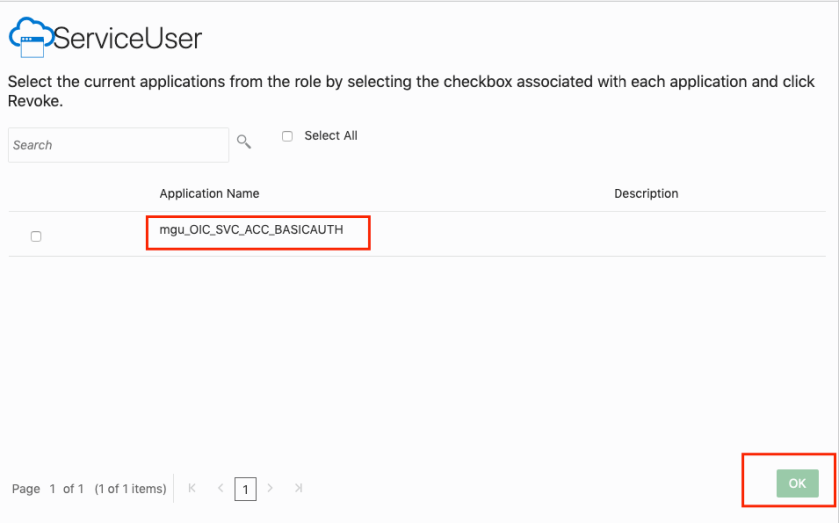
Search for and select the newly created confidential application and click OK.
Now all the configuration related to IDCS Confidential application and association of that application to default OIC application been completed.
Test Hello Word OIC Integration using OAuth Client ID and Client Secret
The final step is to test this configuration, using the Client ID and Client Secret as Authentication parameter to invoke an OIC REST Integration.
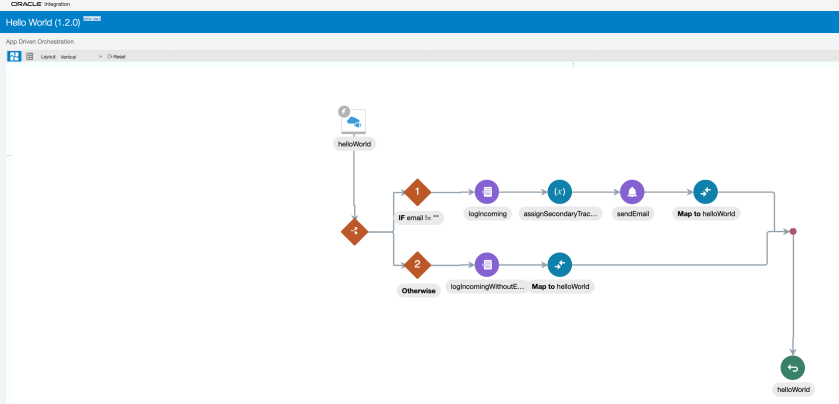
For testing I have chosen “Hello World” Integration which by default gets created during OIC provisioning and ready for invocation. This Integration using REST Adapter (Trigger) Role.
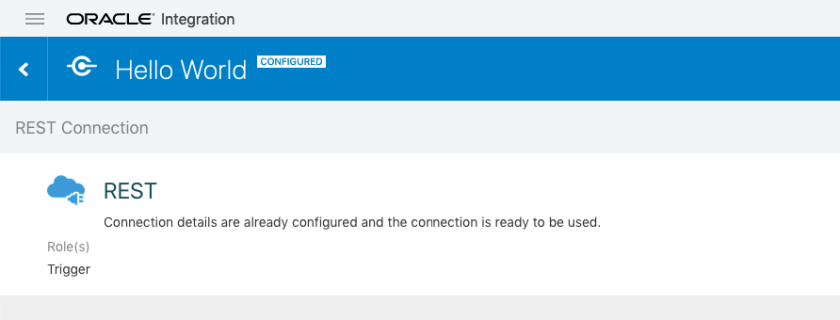
Here is Hello World Integration flow. It echoes back “Hello world” along with name passed in query string while invoking integration
In Postman use the Hello world Integration URL, chose basic auth and pass the Client ID and Client Secret (OAuth Token) to invoke the integration.
Note: This token will never expire. In case if token been compromised then IDCS offers option regenerate client secret. Customer may have one Confidential application shared among multiple Integrations or create multiple confidential applications for different Integrations, completely depends on how they want to structure accessibility of various integrations.
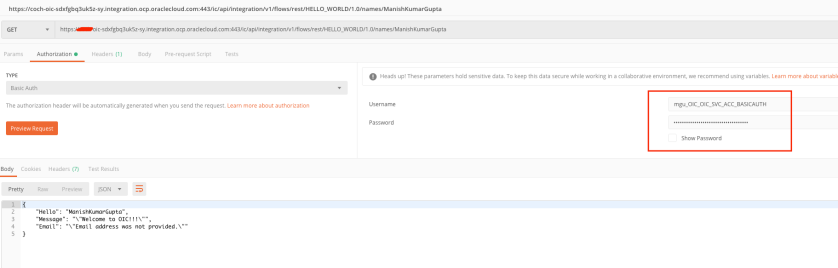
That’s it, the OIC REST Integration was able to be successfully invoked using the client identifiers which will not expire (though they can be revoked from IDCS if required).
Stay tuned for more blogs !!!
Happy Blogging 🙂

Hi Manish
Thank you for an excellent blog.
I am trying to run the curl command(via POSTMAN) to create the IDCS confidential application but getting not authorised error(even though I am using the downloaded token). Any idea why that would be..?
LikeLike
hello, this creation error is happening, can you say why?
{
“schemas”: [
“urn:ietf:params:scim:api:messages:2.0:Error”
],
“detail”: “”,
“status”: “500”
}
LikeLike
Hi, can you specify which step you are finding this error?
LikeLike
This doesn’t work any longer, because in IDCS the OIC instance no longer shows up as an application, so how do we assign the application to an OIC role? The only way I’ve gotten OAuth to work right now is the authorization code method in the ATeam blog from 2018, which pops up a browser window to have you log in, this is not usable in everyday integrations. Would like to know how to set it up to use client credentials, but it no longer works in 2022.
LikeLike
Hi Mike, Depending on your tenancy, there is a transition between those with IDCS access and those managed by OCI IAM. The the OCI console, under “Identity & Security” >> “Federation” then you can see the federated users and groups. By selecting the appropriate user you can create the OAuth Credentials. For either a “federated” user or group, you can now “Manage Roles” (its the banner next to the “Edit” and “Delete” buttons next to the Hero Icon) – here you can assign the service roles (similar to what was available in IDCS). You will still need IDCS Admin access to do this. I hope this helps.
LikeLike
Hi Mike.
This method works perfectly at today (March 2023). If you can’t perform this is because that you committed an error in someone of steps or if you are misconfigured the permissions in th Confidential Application.
Anyway, I recommends use JWT/OAuth Client Credentials authentication instead BASIC auth (ConfApp_BASICAUTH).
LikeLike