Today, Oracle Process Automation with its Recipes helps organizations to reach process excellence faster. The recipes are business process solutions developed with OCI Process Automation (OPA) and available for you once you have provisioned OCI Process Automation service.
Recipes can be deployed as-is, or extended to meet requirements customer-specific.
In addition, to expediting time-to-value for new deployments, the available recipes can be used also as a sort of blueprints for organizations who want to start with new processes built on OPA.
So, just to position the recipes and when better to use them, we can try to post some questions.
- Are you a Developer and looking for quickly deploying new business processes?
- Are you a System Integrator needing to start from a pre-built asset so to be later customized meeting better your needs without reinventing the wheel?
- Are you looking for some samples to be used for demo purposes to test capabilities and functionalities without starting from scratch?
All these questions can find in the OPA Recipes the right answer.
Now, OPA includes the following recipes … and much more will come soon.
- Manage Absence Request
- Manage Discount Requests
- Manage Credit-Increase Requests
- Manage Uniform Requests
Every single Recipe has its own documentation to drive the implementer.
I suggest to carefully look at the system requirements before using those ones; all those recipes are intended only for guidance.
In order to run those recipes, you must perform the following configuration tasks on your Oracle Identity Cloud Service (IDCS) instance in order to successfully run the recipe.
- Assign IDCS application roles
- Create the required users in IDCS
After you’ve configured the roles and other resources, you can activate and run the application and test the process and some capabilities like business searches, how to escalate tasks using the native workspace or the analytics graphical view to see if the process flow is altered by manual intervention.
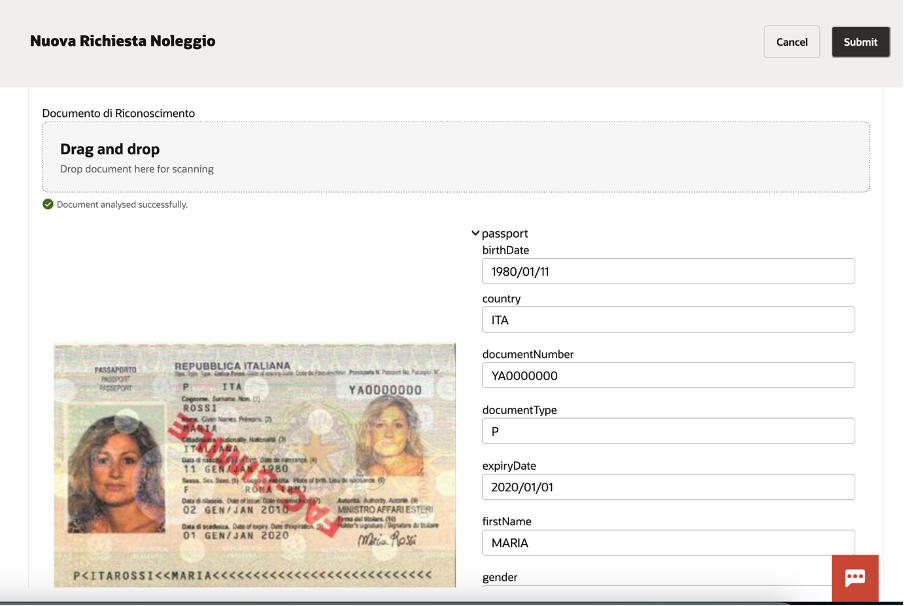
Now you can see how the “Credit Increase Request” can be imported into your own OPA instance:
Create a new process in the application process section

Click on the “Create Application from Recipe” action from the palette:
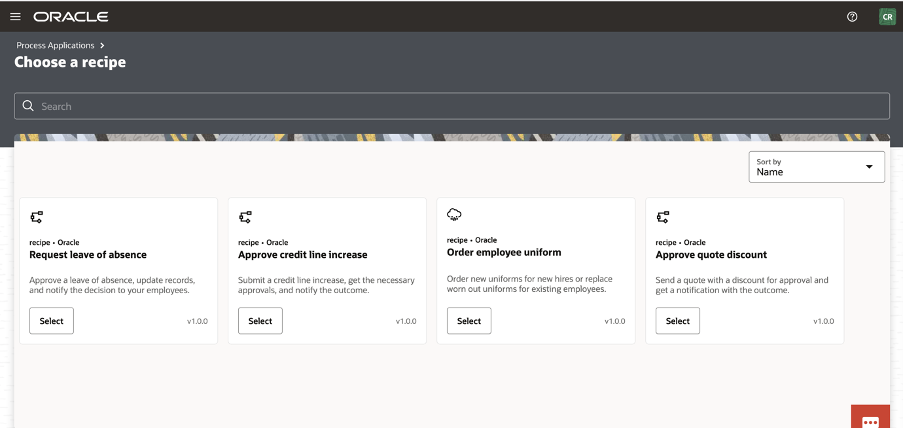
Select, for example, the Approve Credit Line increase

And now, you can see all the artifact imported in your application.

Selecting the “Credit Line Increase Approval” link, you can access the BPMN design of the process

The process is now ready for you to be activated (or customized) selecting the “activate” button at the top of your page

And now ready to be tested in the workspace

You can now start a new request and the web application will appear to you, something like that one here included:
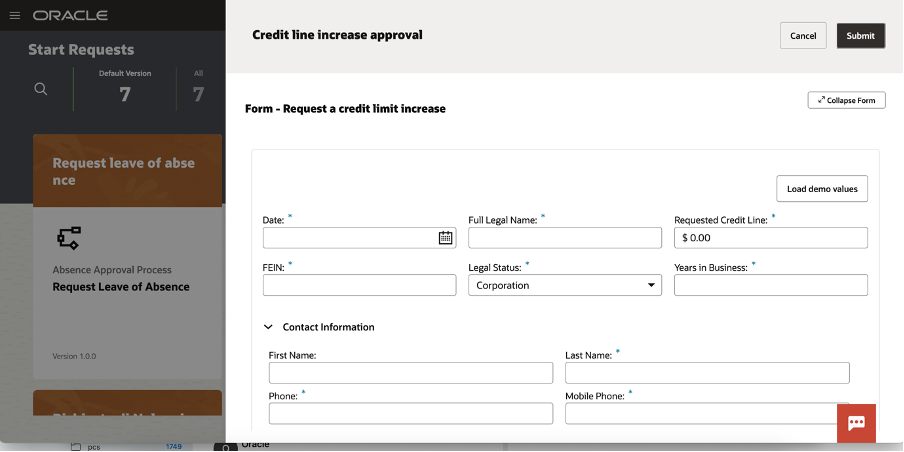
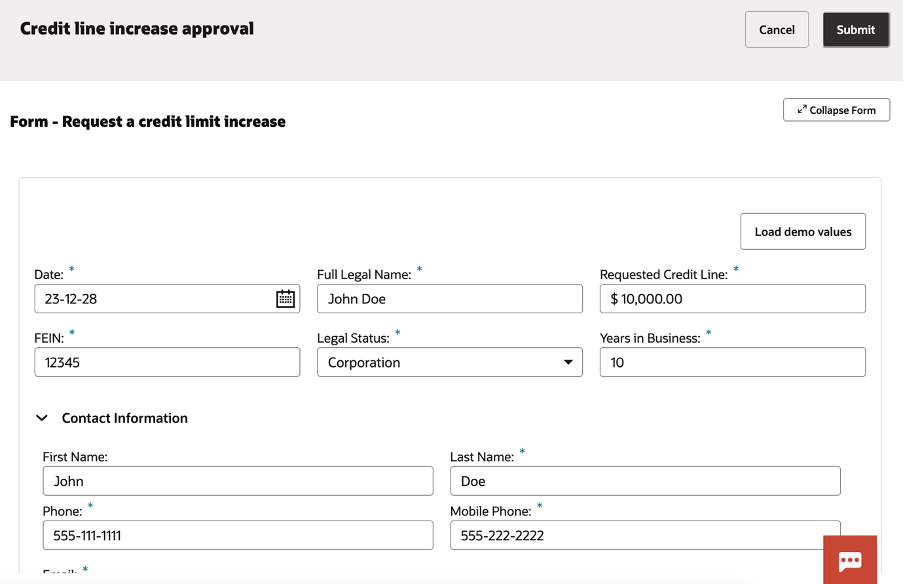
You can load demo values to speed up the test so to quickly see the outcomes of the execution
A new item is now available to be worked by the assignee approving, rejecting, … all the actions that the human workflow will be configured for the specific user, group or application role
As we know, OPA can be used to support business processes to build “system 2 system” or “system 2 human” implementations and when the User Interface is required to interact with the running process you can also modify or extend the web UI leveraging the powerful features to adapt your web page, embedding basic and advanced controls so to drive the business user and simplifying his job reducing errors due to wrong data input
Try it by yourself… it’s a very good accelerator!!
Public and Additional Documentation
https://docs.oracle.com/en/cloud/paas/process-automation/recipes.html
https://www.oracle.com/it/integration/process-automation/features/