One of the most interesting news of the current year is the capability introduced In OIC Gen3 few months ago. I’m talking about the chance we have today to manage events through Oracle Integration.
As we know, often projects require to decouple who can produce messages from who can consume those ones. This approach probably simplifies the integration approach making the applications independent from each other so that any change can be applied, for example, deleting/adding one or more subscribers, without impacting the implementation.
Of course, the decoupling can be built using external messaging queue solutions, something like OCI Streaming Service for which OIC can provide a native adapter or reusing what already used by the customer, for example a Kafka queue, quite common in real use cases.
The first approach probably enables the chance to provide an Oracle Cloud based solution built on top of OCI services delivering in this way an end2end solution based completely on OCI.
The second approach grants the customer to extend and innovate their own applications reusing what already in production adding with Oracle Cloud the most innovative technologies leveraging AI services, Autonomous Database, Oracle SaaS and much more.
At the same time, as explained at the beginning, it’s possible to manage such use cases directly from OIC itself without leveraging other components, or solutions. Everything is managed internally without extra effort in terms of resources or other software to be managed.
What required is to work with “Pub/Sub” pattern… something about the configuration of some actions from the OIC console.
So, to complete the case we need mainly to:
- Create the Event type,
- Create the Publisher,
- Create the Subscriber
1.Create the event type
Starting from scratch we need to configure the event type.
OIC suggests a mockup as a payload just to provide you an example, but you can modify that one to adapt the format to your need in JSON format or eventually you can provide your own XML SCHEMA

2.Create the Publisher
Once defined the message type, it’s required to configure the publisher entity. To do it, you need to set up a new integration flow using one of the available patterns.

To define the Publisher, in my case I have created an integration flow with “Application” style, to include the Publish action from the palette which at runtime will push the message to the embedded event management system included in OIC. As you can see below:

After dragging the activity, you can see something like this:

In the “Publish” action it’s required to configure the Events type … exactly what we have defined during the step 1. In my case, the Event “NewAlarm” is what previously defined.
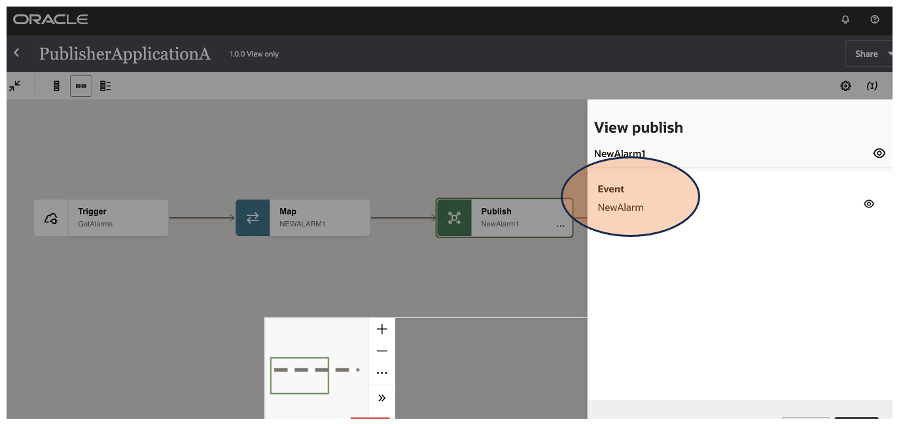
If you don’t have any Subscriber yet, when the publisher fires a new event, this one is retained for you in OIC keeping this one until when a new subscriber consumes that message as below shown:
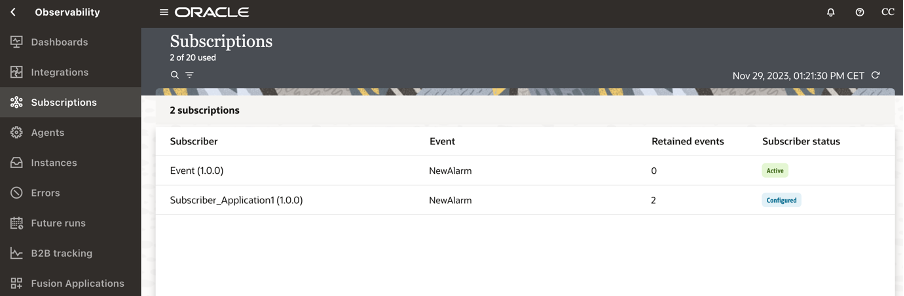
3.Create the Subscriber
The last mile to be covered is about the subscriber. Now we can create a new integration flow for consuming Events as below shown:
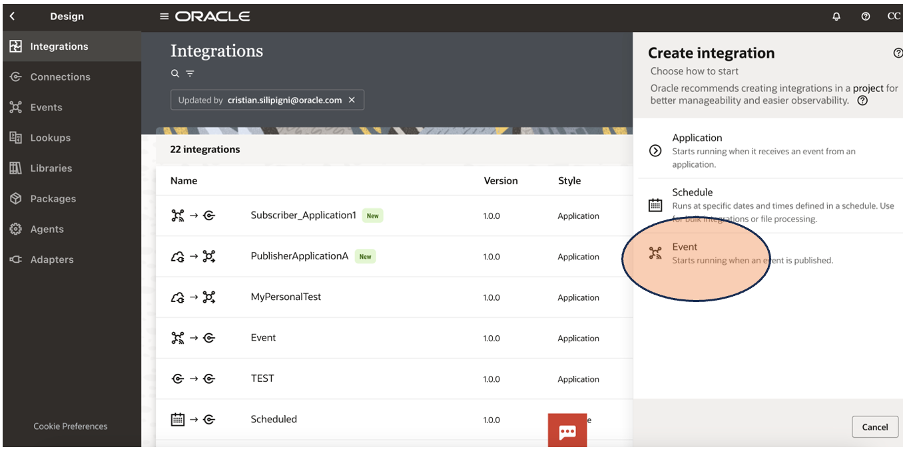
Dragging this activity into your canvas, it’s possible to configure the Subscriber for the interested Event; in my case the “NewAlarm” event previously configured.

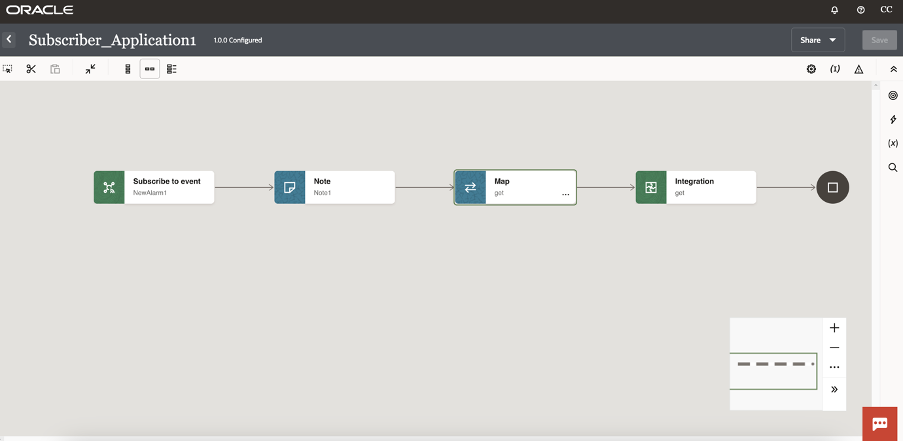
Now you are ready to run your sample just to see how it works.
Monitoring is fundamental to govern and check if everything works fine and above all as expected. Below some screenshots from the OIC console which shows the different levels of monitoring provided natively by the platform

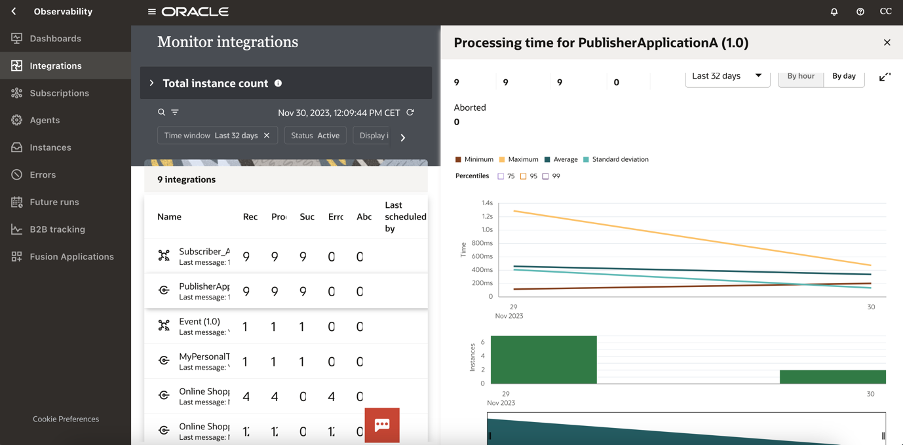


It’s not a demanding activity; quickly you can do it by yourself… to understand how pub/sub pattern works on Oracle Integration
Documentation: